

September 10, 2025
Protecting the Human Layer: Lookout Smishing AI Takes on Next-Gen Social Engineering Threats
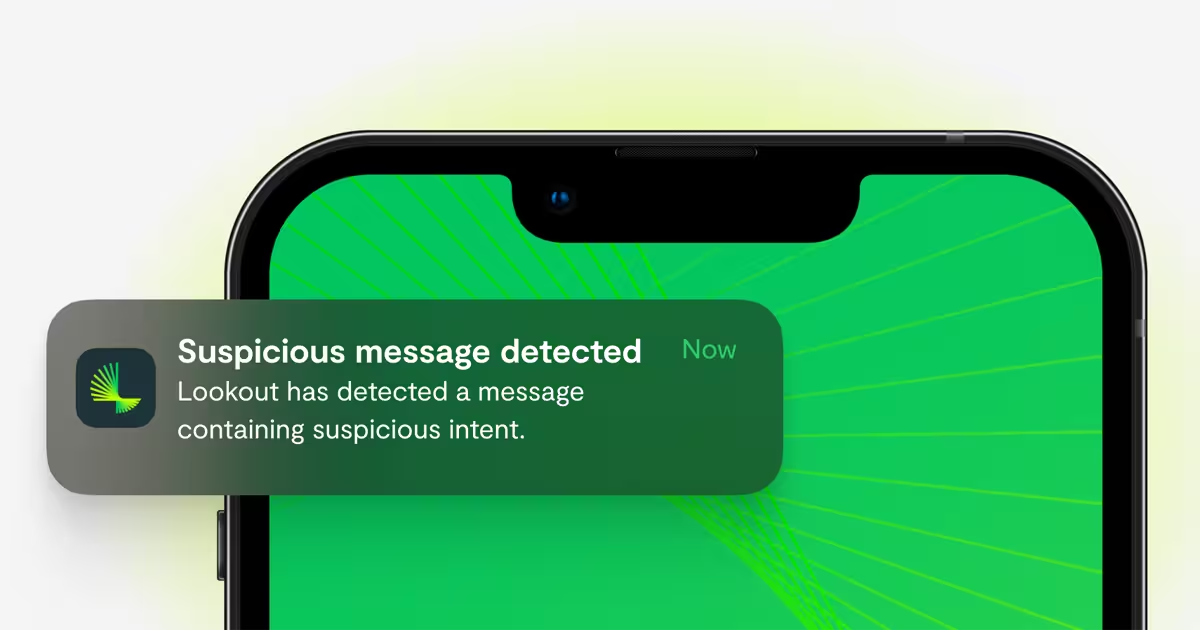
In today's cybersecurity landscape, the most sophisticated attacks often don't target firewalls or servers—they target people. As threat actors leverage AI to craft increasingly convincing social engineering campaigns, employees have become the front line of defense. The mobile device, ever-present and often a repository of personal and professional information, is the primary battleground.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
#
results
#
filters applied


Top Mobile App Security Risks: From Risky Behavior to Hidden Malicious Code
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


BYOD Increases Mobile Phishing Rates, and the Risks Have Never Been Higher
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


No items found.
Insurance and Regulations May Be the Biggest Security Drivers of 2023
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Organizations Are Banning TikTok. Should You Do the Same?
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


A Security Work Stream Is Critical to IT Modernization
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


No items found.
Lookout and Fortra Partner to Secure Sensitive Data Across the Enterprise
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


BYOD and Phishing Attacks: Top Threats Facing US Government
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Q&A With Kristina Balaam: Why Diversity in Cybersecurity Is So Important
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Beyond BEC: How Modern Phishing Has Evolved Past Email
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Work and Life Have Intertwined: Why You Need to Protect Against Phishing
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.



