

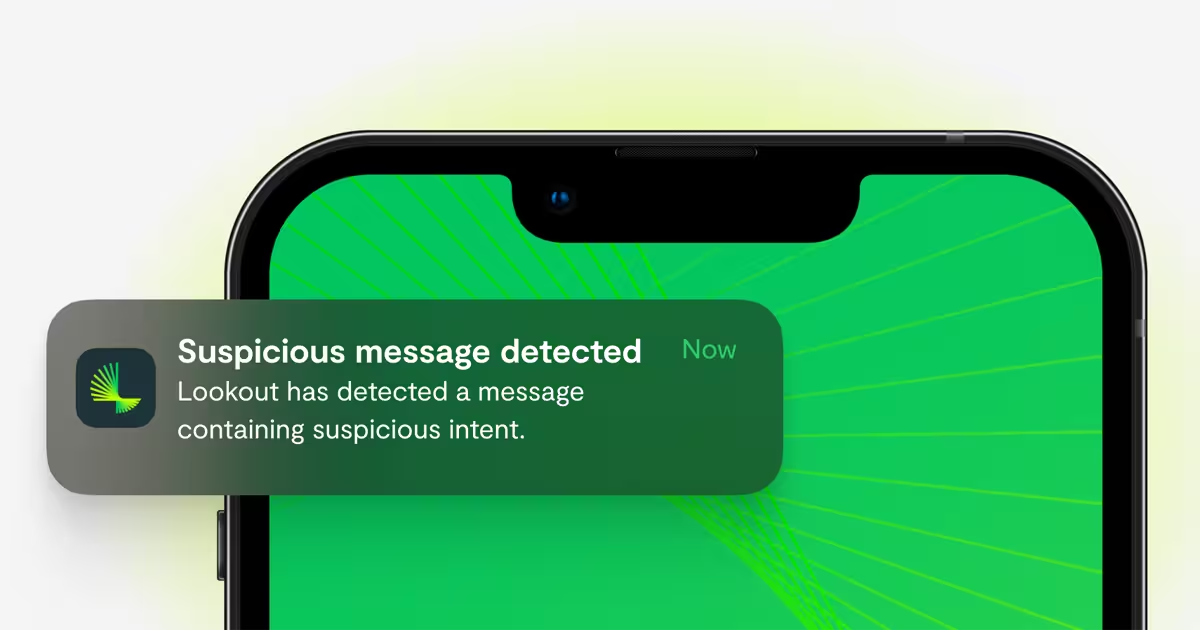
September 10, 2025
Protecting the Human Layer: Lookout Smishing AI Takes on Next-Gen Social Engineering Threats
In today's cybersecurity landscape, the most sophisticated attacks often don't target firewalls or servers—they target people. As threat actors leverage AI to craft increasingly convincing social engineering campaigns, employees have become the front line of defense. The mobile device, ever-present and often a repository of personal and professional information, is the primary battleground.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
#
results
#
filters applied


Navigating BYOD Security: Proven Strategies and Best Practices for Success
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Privacy vs. Mobile Security: Why You Don’t Have to Choose
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


No items found.
Beyond One-Size-Fits-All: Why You Need Security Tailor-Made for Mobile
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Mobile EDR for Security Professionals by Security Professionals
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Busting 6 Myths About Mobile Device Security
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


No items found.
Meet Lookout SAIL: A Generative AI Tailored For Your Security Operations
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Why Should Enterprises Care About APTs? Defend Against Chinese, Russian Cyber Espionage Hacking Groups and Other Nation-State Actors
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


What to Know and What to Do About the MOVEit Vulnerabilities
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


NIST 800-124 Cybersecurity Publication Revision: How to Implement Mobile Security
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Enhancing Mobile Device Security: Applying the NIS2 Directive
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.



