

September 10, 2025
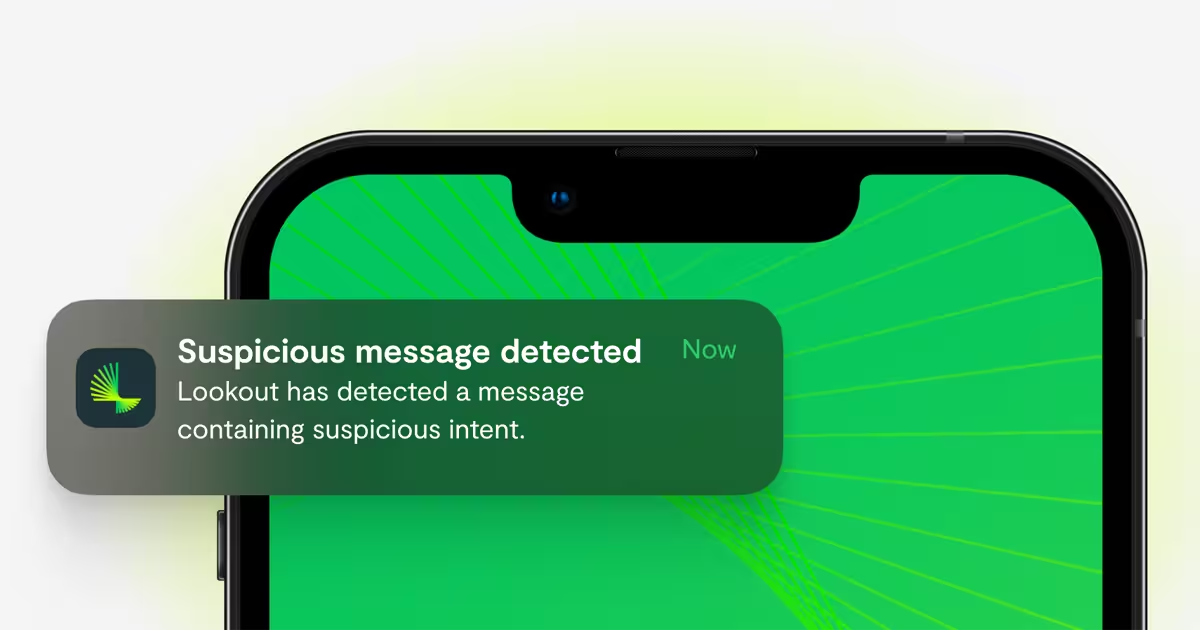
Protecting the Human Layer: Lookout Smishing AI Takes on Next-Gen Social Engineering Threats
In today's cybersecurity landscape, the most sophisticated attacks often don't target firewalls or servers—they target people. As threat actors leverage AI to craft increasingly convincing social engineering campaigns, employees have become the front line of defense. The mobile device, ever-present and often a repository of personal and professional information, is the primary battleground.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
#
results
#
filters applied


The Role of Digital Forensics and Incident Response (DFIR) in Cybersecurity
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Boosting Mobile Defense: A Comprehensive Guide to Mobile Security
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Mastering the Mobile Vulnerability Management Process
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Mobile Endpoint Security: Why Enhancing EDR for Mobile is Critical to Your Organization
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


How to Apply the NIST Framework to Your Mobile Security Strategy
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


CMMC Mobile Security: A Guide to Compliance for Enterprise Organizations
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Mobile Threat Defense: Safeguarding Your Data on the Go
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.
.webp)

How to Use a Risk-Based Vulnerability Management Model to Secure Mobile Devices
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.


Urgent Text from the CEO? Think Twice Before Responding
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.
.webp)

Account Takeover Protection: What It Is and How It Combats ATO Fraud
This is some text inside of a div block.
This is some text inside of a div block.
This is some text inside of a div block.



